The legal & technical tools available today were not designed for the digital world, remote working, or decentralised creation. Without verifiable control, organisations developing IP risk loosing massively due to leakages, legal costs, and reputation damage
Protection of Trade Secrets: Foundation of Intellectual Property
Intellectual property (IP) includes inventions, designs, and other kinds of works of art created by the human brain and subject to copyright law
-- ARM
Intellectual property can constitute more than 80% of a single company’s value
-- ShardSecure
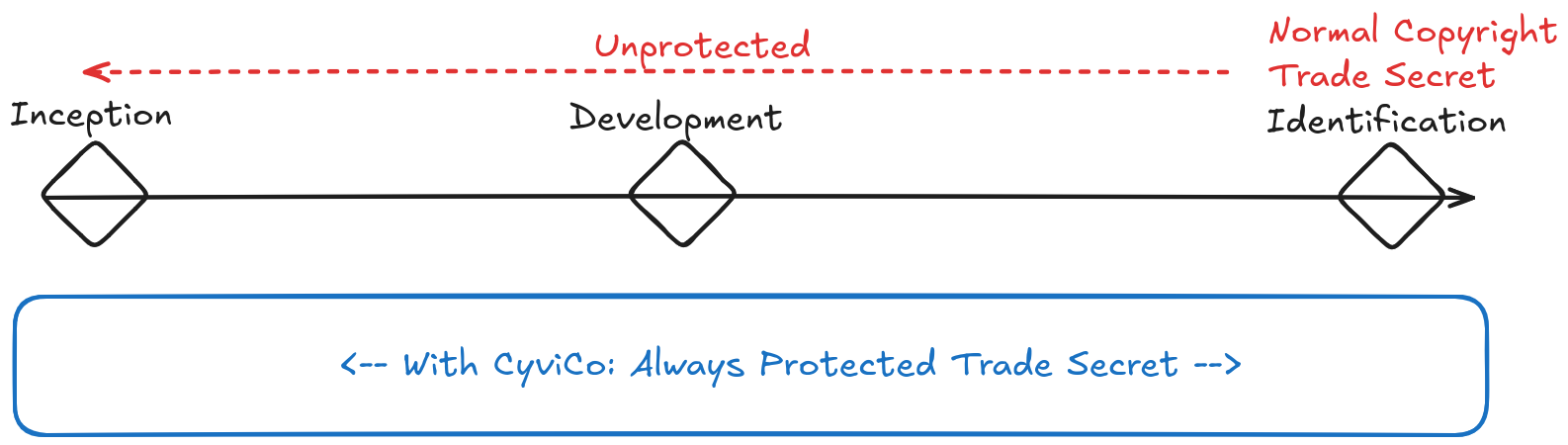
CyviCo is the only technological solution capable of protecting Intellectual Property at the earliest point of relevance, when it first becomes a Trade Secret.
It is irrelevant if the point of inception of the Trade Secret was physically on work premesis or remotely via a remote worker
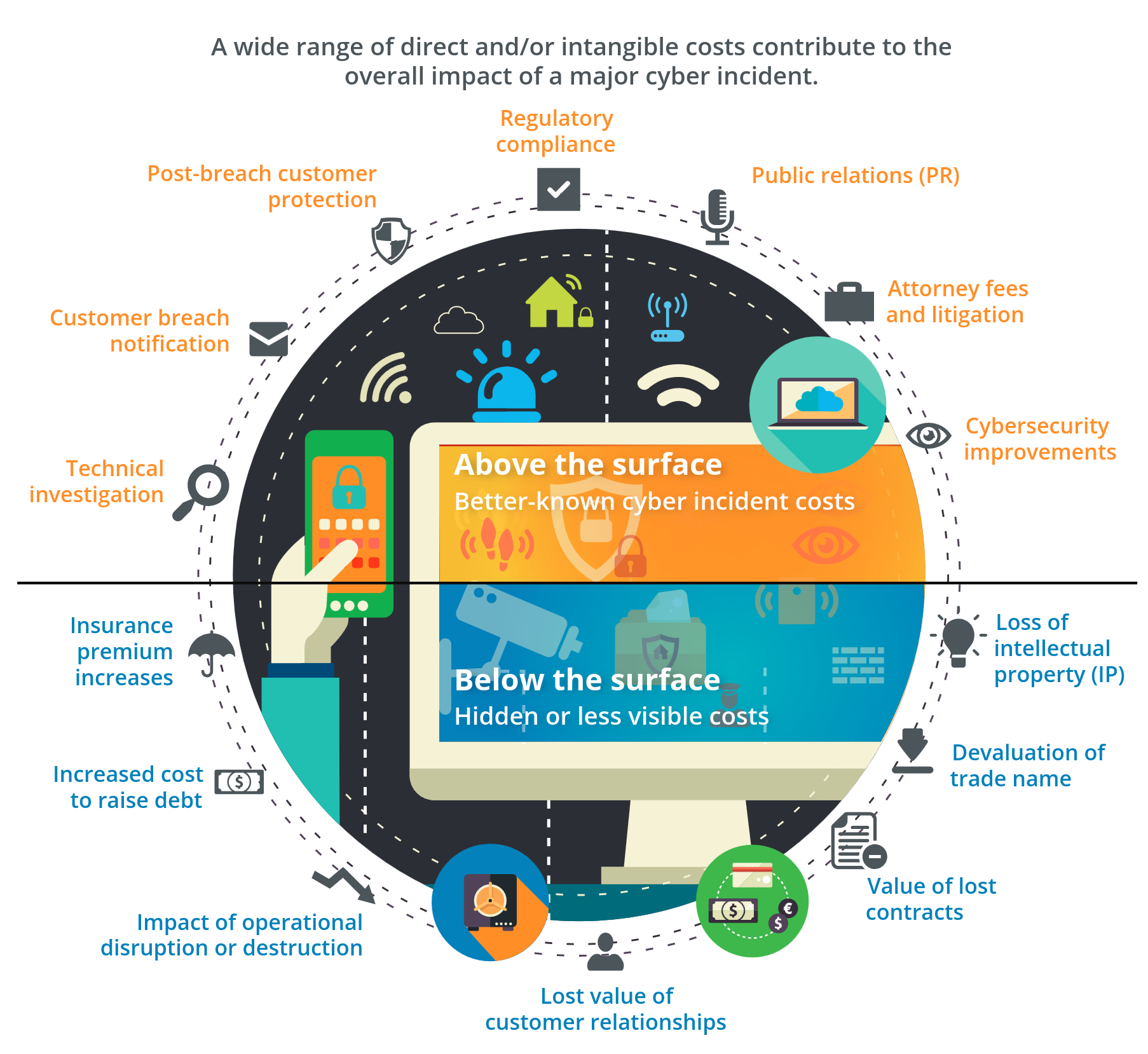
30% value of IP to pay Court Costs
5% of a Countries GDP per year
Weak data security measures may significantly impact the outcome of legal action in IP theft cases. Some courts may calculate a company’s Net Present Value of Future Sales at zero if that company failed to take proper administrative, physical, and technological actions to safeguard their own intellectual property. In the absence of proper IP stewardship, judges have ruled, organizations risk forfeiting their trade secrets entirely
-- Digital Guardian.
Countries must be party to one of several of the following conventions for Copyright to be enforceable (IP Press & Squire Patton Boggs):
-
The Berne Convention (Berne)
-
The Universal Copyright Convention (UCC)
-
The Rome Convention (Rome)
-
The WIPO Copyright Treaty (WCT) (TRIPS Agreement)
-
Digital Millennium Copyright Act (DMCA)
Additionally, some courts have ruled that copying Intellectual Property from Disk to RAM may be a copy for purposes of Copyright Legislation
Copyright does not apply digitally as the original work resides in ephemeral RAM and is destroyed, the file on-disk is a copy of the original.
Unpublished Copyright: Requires original work & evidence of knowledge of such work shared with other people. i.e. Author writes a manuscript and hands it to a few friends to read
Copyright applies to the finished work, not work in progress and is further complicated by End User License Agreements & Terms & Conditions of Use where some companies claim exclusive global license of content passing through their software on route to the storage location.
European Union has put forth the Copyright Term Directive 1993 encouraging dissemination of digital works after death of individual without breach of Copyright; (see Private But Eventually Public: Why Copyright in Unpublished Works Matters in the Digital Age)
All Intellectual Property starts as a Trade Secret per World Intellectual Property Association: [summary of Article 39 of the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS Agreement)]
- Commercially valuable because it is secret,
- be known only to a limited group of persons, and
- be subject to reasonable steps taken by the rightful holder of the information to keep it secret, including the use of confidentiality agreements for business partners and employees
Trade secrets only protect their owner from unauthorized uses of its confidential information in a manner contrary to honest commercial practices.
Honest commercial practices refers to the absence of industrial or commercial espionage, breach of contract, breach of confidence and inducement to breach.
There is no protection if the same information is acquired by another through, for example, independent development or reverse engineering by others, or leakage of confidential information because the owner failed to take reasonable steps to keep it secret, or if the secret becomes generally known within the relevant industry circles.
help users easily find and remember things they have seen on their PC by taking snapshots of their screen and organizing them into a searchable timeline, essentially acting as a "photographic memory"
-- Microsoft "Recall"
Technologies such as Microsoft Recall & Apple Intelligence by their very nature expose the secret beyond the limited tracked copies or knowledge holders breaching the integrity of the Trade Secret.
Fair competition between enterprises is considered as the essential means for satisfying the supply and demand of the economy, and serving the interests of the consumers and the society as a whole... The law of unfair competition, including trade secret law, is considered necessary to ensure the fair functioning of the market and to promote innovation by suppressing anti-competitive business behaviors.
-- World Intellectual Property Organisation - Why is trade secret protection necessary
Only 13 out of 193 member states have varying legislative protocols to support Trade Secrets
Reverse engineering generally doesn’t violate trade secret law because it is a fair and independent means of learning information, not a misappropriation.
CyviCo is an augmentation of CyviZen: Responsibility is Power for commercial requirements, as such automatically inherits:
- Data Ownership,
- CYN: Your Digital Self,
- Hardware Fingerprinting
Additionally, CyviCo provides Profiles guaranteeing Hard Isolation between personal and work data even on personal non-work provided machines. CyviZen & CyviCo Profile Isolation is total, and requires a physical reboot of the machine to switch profiles.
The only way unprotected data can be copied off a CyviZen when using a CyviCo profile without approval is via external visual recording device
This means that CyviCo knows and manages, who you are, on which authorised company profile is in use, and what data permissions are granted at all times.
Remember there are three requirements for Trade Secret:
- Commercially valuable because it is secret, CyviCo ensures that data does not leave the machine without consent.
- be known only to a limited group of persons, CyviCo signs, & verify timestamps as synced against your company systems to know exact time of Trade Secret Creation.
- be subject to reasonable steps taken by the rightful holder of the information to keep it secret, CyviCo totally locks the system down ensuring only those with permission can access the data.
Prevention is better than cure, CyviCo provides total data ownership, isolation, and traceability with the intent of securing Intellectual Property, specifically Trade Secrets as close to inception as possible.
Risk Mitigation is what we utilise in CyviCo through the prevention methodology. This will reduce costs, enhance work processors, ensure an air tight litigation if a cyberattack did transpire, and finally reduce data stealing when employees are made redundant. Our intention is to make the workplace easier to manage while having a greater input from staff and co-workers to get the job done more effectively.