Confidential computing provides a protected Trusted Execution Environment (TEE) to process data out of view of unauthorized software, administrators, or other tenants on shared infrastructure. The data in use is secure; unauthorized parties can’t change it and can’t look at it. That protection extends to the application as well. The TEE helps ensure the integrity of the application, protecting it from tampering or theft.
your data remains your data—no unauthorized users can see it, taint it, or steal it
-- The Linux Foundation: The Case For Confidential Computing
An Operating System for Confidential Computing
System admins and cloud service providers cannot access confidential data while it is being processed
-- OpenMetal
For companies that need to share encrypted datasets, having the computations being done in the TEE ensures data privacy for all parties involved
-- OpenMetal
Data Ownership != Data Confidentiality
CyviZen gives you ownership of your data, meaning you can create, edit or destroy your data at any time irrespective of its location anywhere in the world or on anothers computer.
Data Confidentiality, a key part of Confidential Computing ensures that data can only be opened by authorised users
As a concept, Data Confidentiality is rather simplistic:
- Protect Data at Rest, unmounted disk partitions via encryption such as Linux Unified Key Setup (LUKS)
- Protect Data in Transit, via mutual Transport Layer Security (mTLS) between processes across a network, within processes on the same machine its more challenging
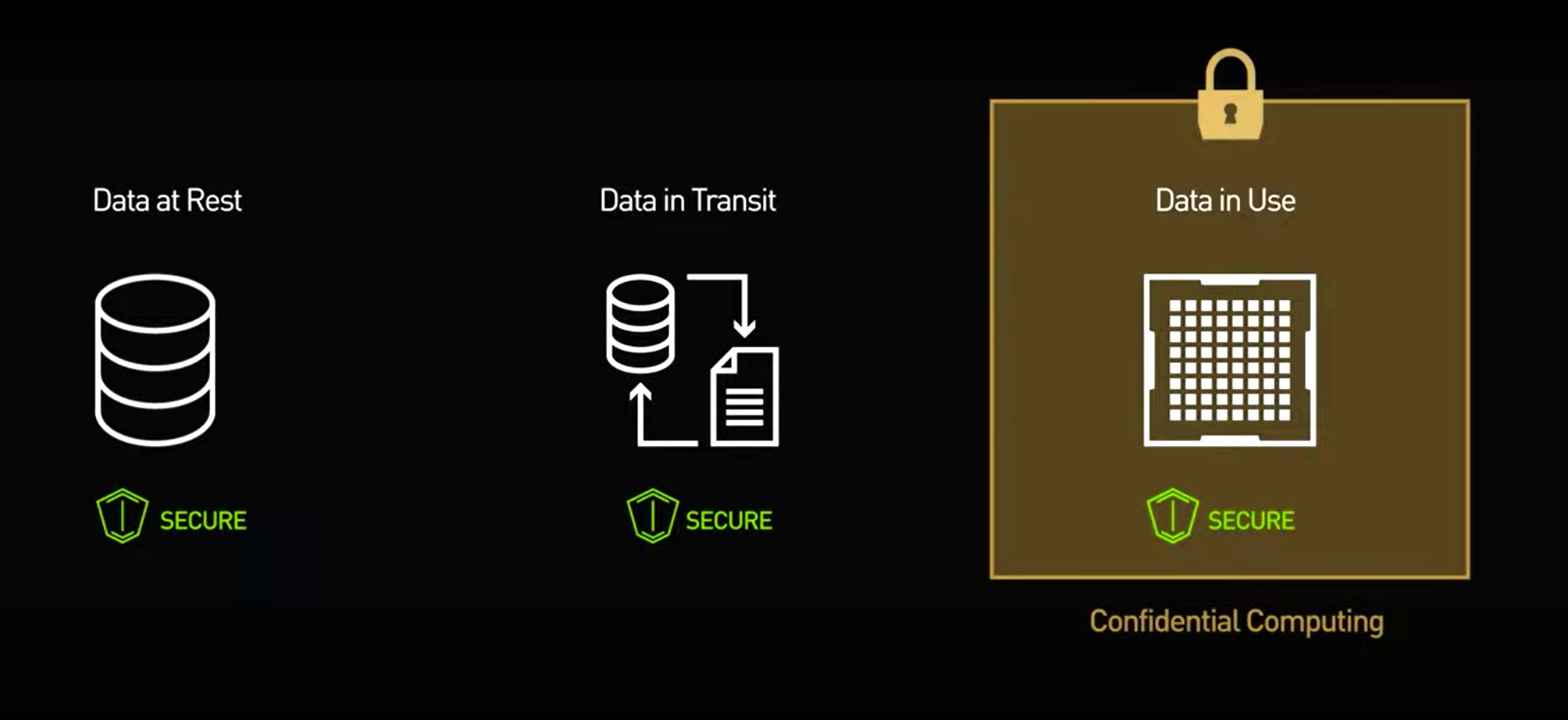
- Protect Data in Use, a hardware based Trusted Execution Environment (TEE) is required such as AMD EPYC to guarantee isolation between processes
TEE can be accessed via a Software Development Kit (i.e. ARM approach), or ideally flexible enough that containers or Virtual Machines can be operated in their entirety within the TEE
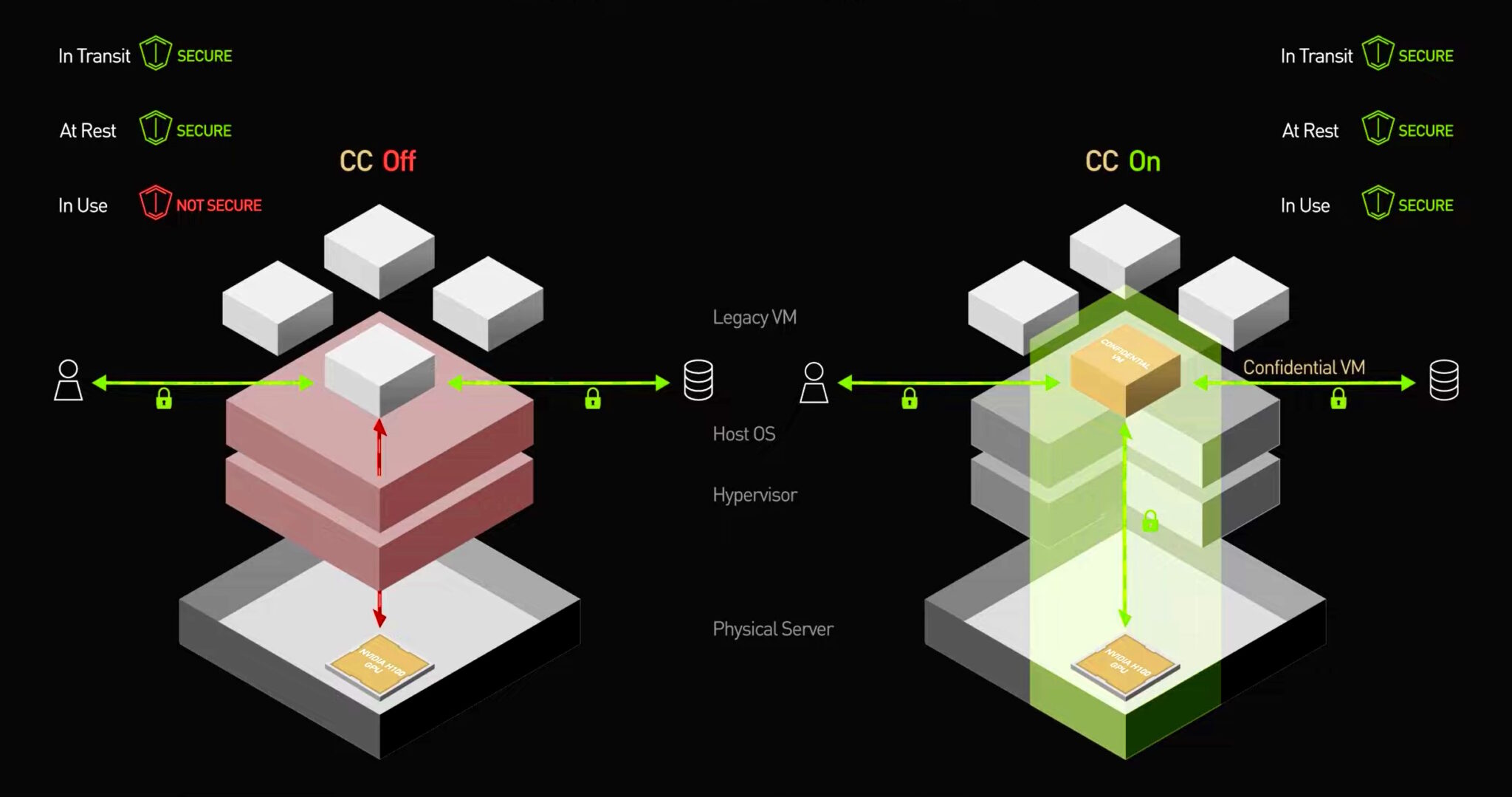
Confidential Computing works best at VM or Container isolation. Whereby the data is passed encrypted into the isolated environment, processed decrypted and re-encrypted prior to being written back to disk.
CyviZen, is designed for Data Ownership in Distributed Environments, significantly more challenging than Confidential Computing, as such CyviZen is capable of being an Operating System for Confidential Computing.
- CyviZen is not suitable as a general purpose operating system for Public Cloud Providers
- CyviZen requires Confidential Computing Hardware, i.e. AMD EPYC when deployed as CyviCo
- CyviZen/CyviCo is compatible with TEE projects:
- Enarx - Confidential Computing with WebAssembly
- Open Enclave SDK - Open source SDK that provides consistent API surface across enclave technologies as well as all platforms from cloud to edge
- Confidential Containers - Deploy Cloud Native Applications inside Confidential Enclaves
CyviZen, the Operating System is designed to handle both secure computing (for when TEE unavailable) & confidential computing. This is due to the unique approach CyviZen uses for:
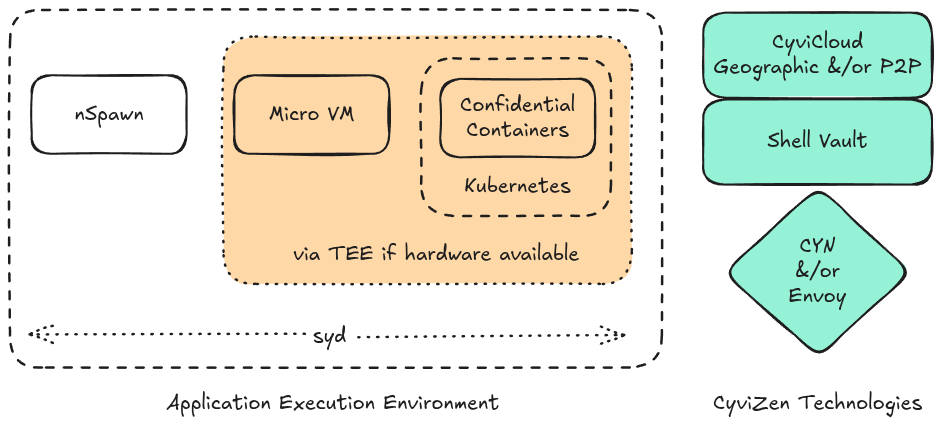
CyviZen is capable of wrapping any App with Syd a Rock-Solid Application Kernel that implements a subset of the Linux kernel interface in user space, intercepting system calls to provide strong isolation without the overhead of full virtualization. Syd is secure by default, and intends to provide a simple interface over various intricate Linux sandboxing mechanisms such as LandLock, Namespaces, Ptrace, and Seccomp-{BPF,Notify}
CyviCo is an augmentation of CyviZen: Responsibility is Power for commercial requirements, as such automatically inherits:
- Data Ownership,
- CYN: Your Digital Self,
- Hardware Fingerprinting
- CyviZen Secure & Confidential Computing Design
CyviCo works best on AMD EPYC Confidential Computing with your environments executing via Micro Virtual Machines (512MB RAM). Both CyviCo & the Micro VMs are fully configurable and can be dynamically reconfigured on the fly. Additionally, CyviCo supports Kubernetes & Confidential Containers
CyviCo via CyviZen is immutable, so updates to the Confidential Computing machine are best viewed as swappable instead of permanent as any of the last 10 assembled systems can be swapped to at any time without conflict or issue.